One of the challenges for business development and proposal teams is making sure they are aware of the technical, schedule, and cost implications of complying with all regulatory requirements when they submit a response to a government request for proposal. This now includes the Cybersecurity Maturity Model Certification (CMMC) framework of processes and best practices the Office of the Under Secretary of Defense for Acquisition and Sustainment (OUSD(A&S)) has recently developed.
The goal of the CMMC is to establish a standard foundation of information security the industrial base practices to stem the loss of intellectual property and other unclassified information. The DoD needs assurance that a contractor can adequately protect their intellectual property, proprietary information, technical information, and information systems from unauthorized disclosure or malicious attackers before they do business with that contractor.
Similar to other maturity models, the CMMC framework provides the DoD with the means to verify and certify a contractor has implemented the necessary processes and practices to achieve a defined level of cybersecurity capability. This has become critical for all of the unclassified data and systems in the defense industrial base (DIB) as a matter of economic and national security.
CMMC merges several cybersecurity control standards that have been in place for a number of years into a single standard that is more comprehensive and can be objectively verified. This includes the NIST Special Publication (SP) 800-171, Protecting Controlled Unclassified Information in Nonfederal Systems and Organizations referenced in the DFARS Clause 252.204-7012, Safeguarding Covered Defense Information and Cyber Incident Reporting.
CMMC has broad implications for all contractors directly or indirectly doing business with the DoD or that want to do business with the DoD. It encompasses the entire multi-tiered supply chain including companies that provide commercial off the shelf (COTS) products and services. CMMC requires the defense industrial base to become certified once the CMMC is fully integrated into the DoD acquisition process.
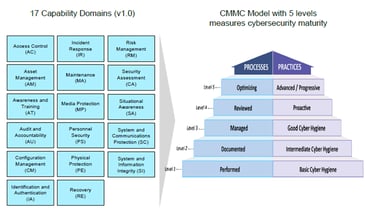
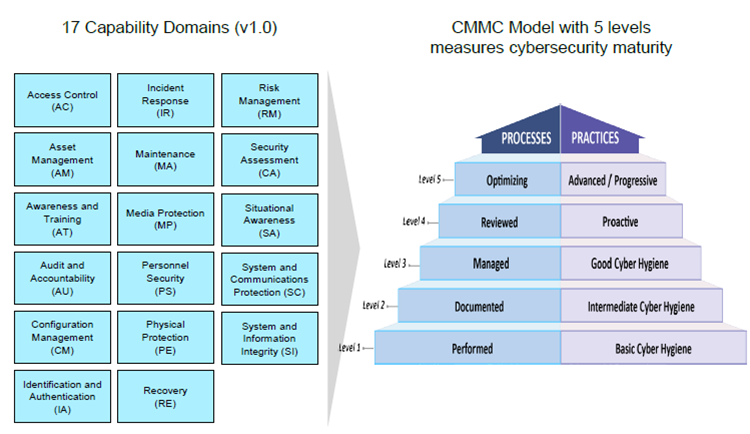
The CMMC levels, descriptions, and 17 capability domains are illustrated below. This image is from the CMMC public briefing available on the OSD CMMC web site.
What’s the impact to proposal teams?
Proposal teams should be prepared to start seeing CMMC language in requests for proposals and requests for information. DoD’s intent is that by 2026, all new contracts will specify the level of CMMC certification that applies. Compliance will be enforced and mandatory for all contract awards.
That means contractors must be prepared to achieve a specific CMMC level that is commensurate with the level of information to be protected. Contractors must be certified by a CMMC Third Party Assessment Organization (C3PAO). As of September, 2020, the requirements for becoming an assessment organization haven’t been established. These requirements should begin to roll out in the coming months. For the latest information on approved CMMC Third Party Assessment Organizations, visit the CMMC Accreditation Body (AB) web site.
We are all learning the lexicon of information security and why it is critical to protect the industrial base against cyber-attacks. We also need to be aware of the potential for Federal Contract Information (FCI) and Controlled Unclassified Information (CUI) “leakage” and how to mitigate it starting with the proposal phase of a contract.
The cost estimating and pricing data as well as the basis of estimate narrative information is proprietary or competition sensitive information. Since the RFP statement of work also includes technical requirements, the proposal response is likely to include other proprietary technical specifications, drawings, or other sensitive data.
As they develop their cost estimates, proposal teams need to be aware of:
- Current internal initiatives to implement increasingly robust cybersecurity processes and practices as part of the normal way of doing business. How do those initiatives align with the CMMC levels of maturity? And, what is the time line for implementing the processes and practices? This matters at a number of levels. For example:
- Resource requirements and where work is performed impacts the cost estimate details and assumptions. Does the proposal team need to include additional technical resources or plan for the work to be performed at a US based facility instead of a foreign facility to support cybersecurity requirements in the proposal? What about the information systems environment? Is it maintained internally or cloud-based? The proposal team will need to be aware of where data is maintained and information security mechanisms in place.
- Overhead rates used to price the proposal. The costs for achieving and maintaining the desired level of cybersecurity capability is a cost of doing business that will need to be incorporated into forward pricing rates. The basic assumption is that all contractors understand that implementing information security best practices is a fundamental business requirement. It must be a corporate commitment to follow best practices and ingrained into how people go about doing their jobs.
- How the team responds to Sections L (Instructions, Conditions, and Notices) and M (Evaluation Factors for Award) in the RFP related to cybersecurity. Once CMMC is fully integrated into the DoD acquisition process, Sections L and M will specify the certification level required for you and your suppliers. Proposal teams will need to be able to respond “Yes” for your company to be awarded the contract. In meantime, they should be able to talk to current initiatives and target dates to achieve cybersecurity goals.
- Supplier cybersecurity capabilities. Proposal teams must be aware of supplier cybersecurity processes and practices. Cybersecurity requirements will need to be defined as part of the procurement process and incorporated into the contracts with the suppliers. It may be necessary to identify different suppliers and potentially eliminate others who do not meet certain basic requirements. Another blog on documenting supplier BOEs discussed the impact of recent regulatory requirements for identifying foreign suppliers or suppliers using specific equipment from foreign entities. Procurement personnel as well as the proposal team will need documentation or other means to objectively verify a supplier has achieved a specific CMMC level of maturity and include this in the proposal response. This will become easier with time as more contractors become certified.
How can the right basis of estimate software help?
This is where ProjStream’s BOEMax basis of estimate software can support access control cybersecurity initiatives and prevent information “leakage.” BOEMax is designed for proposal teams to organize their cost estimating, pricing, and basis of estimate narratives in a single, central database so they have better control of the proposal cost estimate data and who can access the data.
With BOEMax, proposal teams can:
- Eliminate spreadsheets and other non-integrated proposal content that could be susceptible to information “leakage” when there are a number of ad-hoc components in the proposal process. Rather than trying to manage a raft of separate Excel spreadsheets, MS Word documents, and other related technical information materials often scattered on different servers or desktops, they can organize the proposal content into one BOEMax project using the framework of the WBS.
- Control who has access to the proposal project data at the application level that align with your corporate cybersecurity processes and practices. System level administrators determine who can access BOEMax and specific BOEMax proposal projects. BOEMax can be deployed on internal corporate servers or in a secure cloud environment in accordance with your internal system security and access controls.
- The authorized subject matter experts (SMEs) and members of the proposal team can all access the same single source project to develop or review the work elements they are responsible for using an Excel-like interface. This streamlines the development process and improves the quality of the data because the team doesn’t need to merge content from disparate spreadsheets or documents. They can also include their narrative text and technical documents with their cost estimate data in the same database.
- Document supplier cybersecurity capabilities in the BOEMax database so it is automatically included in the cost estimate proposal documents.
- Use the built-in workflow to manage the development and approval process. The audit log provides the proposal manager with full traceability of who made what changes to the data.
Interested in seeing how BOEMax can simplify life for your proposal teams? Call us today to schedule a demo.
Updated September 25, 2020